Federal Investigation: Millions Stolen Via Executive Office365 Hacks
Table of Contents
The Scale of the Problem: Executive Office365 Security Breaches
The widespread nature of Office365 breaches is staggering, impacting businesses of all sizes and across various industries. These breaches aren't just isolated incidents; they represent a significant and growing threat to financial stability and data security. The financial losses associated with these attacks are mounting, with millions of dollars lost due to compromised accounts. The frequency of targeted phishing attacks and the sophistication of the malware used are also on the rise.
Statistics paint a grim picture. While precise figures from the ongoing federal investigation are still emerging, reports suggest a dramatic increase in successful Office365 hacks over the past year. This is further compounded by the fact that many breaches go unreported, leading to an underestimation of the true scale of the problem. High-profile cases involving significant financial theft from compromised Office365 accounts have further fueled concerns.
- Millions lost due to compromised Office365 accounts.
- Increased frequency of targeted phishing attacks specifically designed to bypass multi-factor authentication.
- Sophisticated malware exploiting zero-day vulnerabilities and evading traditional security measures.
- Data breaches leading to identity theft, reputational damage, and regulatory fines.
Methods Used by Cybercriminals in Office365 Hacks
Cybercriminals employ a range of sophisticated techniques to breach Office365 security. These attacks often leverage a combination of methods to maximize their chances of success. Common hacking techniques include:
-
Phishing: This remains a highly effective tactic. Hackers send deceptively realistic emails mimicking legitimate communications from trusted sources, such as banks or internal IT departments. These emails often contain malicious links or attachments that deliver malware or attempt to steal credentials. The sophistication of these phishing attempts continues to improve, making them increasingly difficult to detect.
-
Credential Stuffing: This technique uses stolen usernames and passwords from other data breaches to attempt access to Office365 accounts. Hackers acquire these credentials from various sources on the dark web and systematically test them across different platforms, including Office365. This highlights the importance of using strong, unique passwords for each account.
-
Malware: Sophisticated malware is used to gain unauthorized access to accounts and systems. Once inside, hackers can steal data, install backdoors, and maintain persistent access. This malware often exploits vulnerabilities in Office365 or its integrated applications.
-
Exploiting Vulnerabilities in Third-Party Apps: Many organizations integrate third-party apps with Office365, potentially creating vulnerabilities if those apps are not properly secured. Hackers often exploit weaknesses in these applications to gain access to the main Office365 environment.
The Federal Investigation and its Implications
The ongoing federal investigation into the Office365 hacks is a significant development, highlighting the seriousness of the threat and the determination of authorities to address it. The investigation aims to identify the perpetrators, dismantle their operations, and recover stolen funds. This collaboration between federal agencies and the private sector is crucial to combatting this evolving threat.
- Focus of the investigation: Identifying the perpetrators and their methods of operation.
- Collaboration between federal agencies and private sector: Sharing information and resources to improve cybersecurity defenses.
- Potential for increased regulatory scrutiny: Organizations with inadequate security practices may face increased scrutiny and potential penalties.
- Legal ramifications: Businesses that fail to maintain adequate security may face lawsuits, fines, and reputational damage. The penalties for non-compliance with data protection regulations are substantial and are likely to increase.
Protecting Your Organization from Office365 Hacks
Protecting your organization requires a multi-layered approach to cybersecurity. Implementing robust security measures is not just a best practice; it's a necessity.
- Implement strong password policies and MFA (Multi-Factor Authentication): Enforce the use of complex passwords and enable MFA to add an extra layer of security.
- Regularly update software and patches: Keep your Office365 applications, operating systems, and security software up-to-date to mitigate vulnerabilities.
- Use reputable security software and anti-malware solutions: Implement robust anti-malware and anti-phishing solutions to detect and prevent threats.
- Conduct regular security audits and penetration testing: Identify and address vulnerabilities before hackers can exploit them.
- Implement robust data loss prevention (DLP) measures: Prevent sensitive data from leaving your organization's network unauthorized.
- Invest in regular security awareness training for employees: Educate your employees on phishing techniques and safe computing practices.
Conclusion
The federal investigation into the millions stolen via Executive Office365 hacks underscores the critical need for enhanced cybersecurity measures. The sophistication of these attacks and the significant financial losses highlight the vulnerability of relying solely on cloud-based services without robust security protocols. By implementing the preventative measures outlined above, organizations can significantly reduce their risk of becoming victims of similar attacks. Don't wait until it's too late – proactively strengthen your Executive Office365 security today to prevent becoming another statistic in this growing trend of Executive Office365 security breaches. Take control of your data and protect your business from the devastating impact of an Office365 hack. Invest in your security and protect your future.

Featured Posts
-
 Federal Investigation Millions Stolen Via Executive Office365 Hacks
Apr 22, 2025
Federal Investigation Millions Stolen Via Executive Office365 Hacks
Apr 22, 2025 -
 Is Blue Origins Failure More Significant Than Katy Perrys Career Missteps
Apr 22, 2025
Is Blue Origins Failure More Significant Than Katy Perrys Career Missteps
Apr 22, 2025 -
 Top Chinese Indonesian Officials Strengthen Security Cooperation
Apr 22, 2025
Top Chinese Indonesian Officials Strengthen Security Cooperation
Apr 22, 2025 -
 Return To Classes At Fsu After Deadly Shooting Students And Faculty React
Apr 22, 2025
Return To Classes At Fsu After Deadly Shooting Students And Faculty React
Apr 22, 2025 -
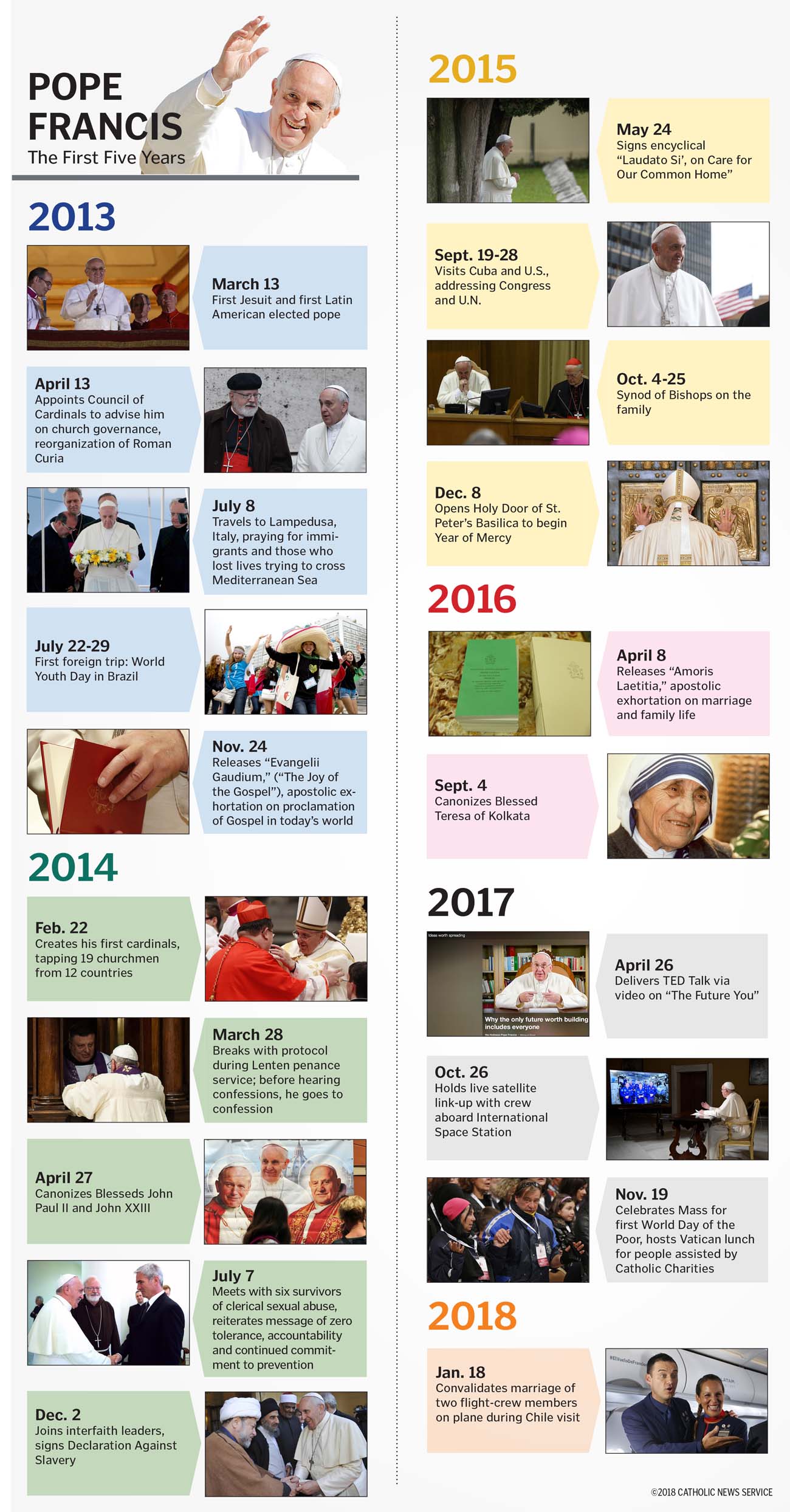 The Next Pope How Francis Papacy Will Shape The Conclave
Apr 22, 2025
The Next Pope How Francis Papacy Will Shape The Conclave
Apr 22, 2025
